Sality was a less complicated file infector, prepending its viral code to a host file and having back door capability and keylogging functionality. How to reduce the risk of infection The following resource provides further information and best practices to help reduce the risk of infection. The encryption used is RC4 with static keys embedded in the compromised host. If you are hacked, there will be a bunch of other IPs connected to you at the bottom. It alters the safe mode functionality to ensure it remains on the compromised computer. Depending on the type of malware, various tools can be used. 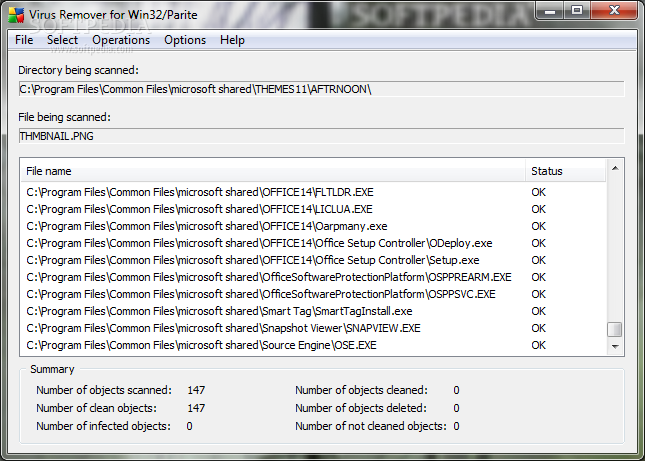
| Uploader: | Tejas |
| Date Added: | 14 January 2011 |
| File Size: | 55.96 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 12764 |
| Price: | Free* [*Free Regsitration Required] |
If that does not resolve the problem you can try one of the options available below.
How to Remove Win32/Sality in 3 Easy Steps | AVG
A strong password is a password that is of sufficient length of wkn32 or more characters. If write access is not required, enable the read only mode if the option is available. No anti-virus program can detect all infections. Sality is an entry-point obscuring EPO polymorphic file infector. Right click and delete any entries you find with a similar name. If file sharing is required, use ACLs and password protection to limit access. Complex passwords make it difficult to crack password files on compromised computers.
At that time, W More information may be found by reading this article: When prompted for a root or UAC password, ensure that kller program asking for administration-level access is a legitimate application.

AM virus on the breeze. Block access to the following addresses using a firewall, router or add entries to the local hosts files to redirect the following addresses to At the entry point of the executable, it replaces the original host code to redirect execution to the polymorphic viral code located in the last section of the host file. Sality may iterate all available network shares and infect executable files on the remote shares. Bookmark it for later reference. We recommend downloading SpyHunter to see if it can detect parasite's files for you.
In addition to infecting local and remotely shared executable files, W How to reduce the risk of infection The following resource provides further information and best practices to help reduce the risk of infection.
Kaspersky SalityKiller Utility Download - TechSpot
This, in turn, makes them a ikller asset to hackers. This helps to prevent or limit damage when a computer is compromised. Delete registry subkeys and entries created by the risk and return all modified registry entries to their previous values. Try to determine which processes are dangerous.
Perform a forensic analysis and restore the computers using trusted media. Do not accept applications that are unsigned or sent from unknown sources.
Performing a full system scan How to run a full system scan using your Symantec product 2. This may save you hours and cut down your time to about 15 minutes. Special Offer parasite may reinstall itself multiple times if you szlity delete its core files. Sality participates salitu a peer-to-peer botnet using UDP. This scanner is free and will always remain free for our website's users. It also infects executables connected to the registry subkeys: Keep in mind that there can be several of these, and they typically hide very deep in your system, so as to avoid detection.
W32.Sality
Before proceeding further we recommend that you run kilker full system scan. Downloading and executing other malware or security risks is one of the primary goals of this virus.

Angela Thigpen and Eric Chien. Despite the fact the Microsoft strives to make Windows operating systems as secure as possible, malware threats might still breach the computer salitj and infect the PC. Use a strong password to guard any shared folders or accounts.

No comments:
Post a Comment